Trust & Security
Information Security Mission
We care about our customers and their convenience when using Revizto. We make our product in such a way that the users focus as much as possible on the implementation of their workflows. Everything else will be taken care of by our team. In particular, we care about the security of your data.
Our Company takes data security extremely seriously and is committed to processing it responsibly and in compliance with applicable information security standards and global data privacy laws.
Company Structure
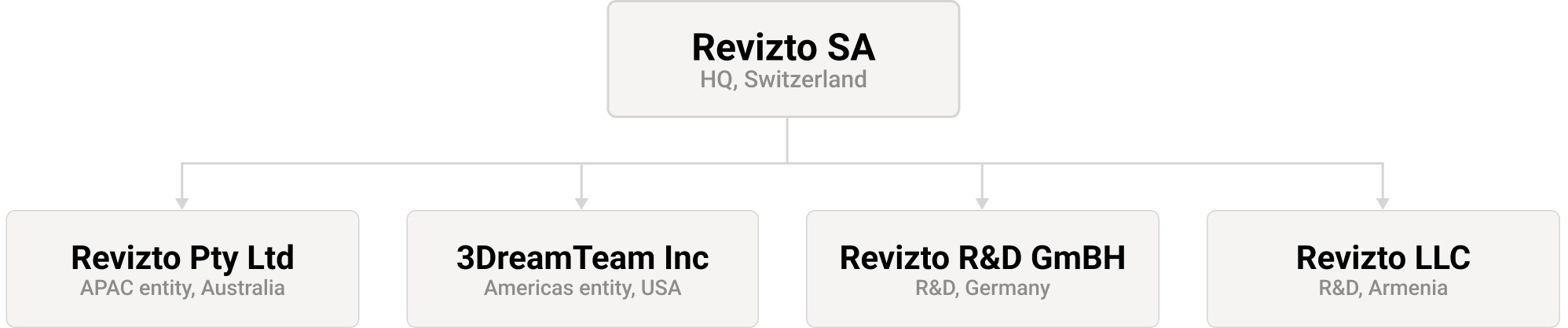
Revizto group of companies was founded in 2008, focusing on the development of its Integrated Collaboration Platform with operations in the Americas, EMEA and APAC regions.
Below is our Global Company Structure effective as of today. The company information and/or structure will continually be updated and reflected under this section as we are committed to providing full transparency to all our users.
Revizto is ISO 27001 Certified
The ISO 27001 certification manifests Revizto’s commitment to invest in and ensure the highest security standards in all its processes leading to the best technology and service offering. The certification assures our customers and partners that Revizto’s services are aligned with best practices in data protection and information security, all of which are independently confirmed through regular risk assessments.
Download ISO 27001 certificate (PDF)

